Recent Score:
Take the Test again Go Home
Azure Compute Services Illustration Slideshow
1
What is the effect of the default network security settings for a new virtual machine?
- Outbound request are allowed. Inbound traffic is only allowed from within the virtual network
- Outbound requests are considered low risk, so they are allowed by default. Inbound traffic from within the virtual network is allowed. By placing a VM in a virtual network, the VM owner is implicitly opting-in to communication among the resources in the virtual network.
2
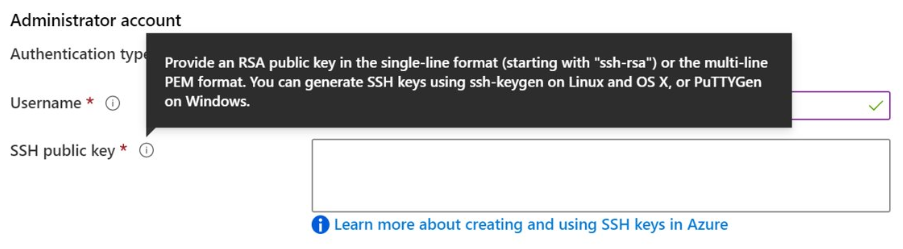
Suppose you have several Linux virtual machines hosted in Azure. You will administer these VMs remotely over SSH from three dedicated machines in your corporate headquarters. Which authentication methods would typically be considered best-practice for this situation?
- Private key access with a passphrase is the most secure option. Even if an attacker acquires your private key, they will be unable to use it without the passphrase.
3
When creating a Windows virtual machine in Azure, which port would you open using the INBOUND PORT RULES in order to allow remote-desktop access?
- The Remote Desktop Protocol (RDP) uses port 3389 by default so this port is the standard port you would open if you wanted to use an RDP client to administer your Windows virtual machines.
4
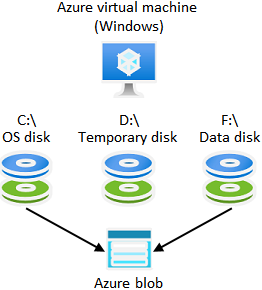
Suppose you have an application running on a Windows virtual machine in Azure. What is the best-practice guidance on where the app should store data files?
- Dedicated data disks are generally considered the best place to store application data files. They can be larger than OS disks and you can optimize them for the cost and performance characteristics appropriate for your data.
5
What is the final rule that is applied in every Network Security Group?
- Deny all. It will block all traffic that you don't specifically allow.
6
Suppose you're an administrator of several Azure virtual machines. You get a text message indicating some problems with your VMs. You are at a friend’s house and only have your tablet with you. True or false: you'll still be able to access the Azure CLI using the tablet, even though you can't install the CLI on it.
- True: The Azure Cloud Shell is available in the browser and runs with the full Azure CLI. If you prefer Powershell, the Azure Cloud Shell has that as well.
7
Suppose you have a script that creates several VMs with different images. When the script issues the command to create the first VM you do not want to block the script while the VM is created, instead you want the script to immediately move on to the next command. What is the best way to do this?
- Adding '--no-wait' will cause 'azure VM create' to return immediately without waiting for the VM to actually be created.
8
Most Azure commands return JSON by default. Sometimes this data set can be very large which makes it difficult to read and tricky to use the result of one command as input to another command. What can you use with Azure CLI to filter the results to get only the data that you need?
- All Azure commands support the '--query' argument which lets you select the useful data in any Azure command response.
9
Which workload option should be selected to run a network appliance on a virtual machine?
- Compute optimized virtual machines are designed to have a high CPU-to-memory ratio. Suitable for medium traffic web servers, network appliances, batch processes, and application servers.
10
An organization has a security policy that prohibits exposing SSH ports to the outside world. What is the best way to connect to the Azure Linux virtual machines and install software?
- The Azure Bastion service is a new fully platform-managed PaaS service provisioned inside a virtual network. Bastion provides secure and seamless RDP and SSH connectivity to virtual machines. The access uses the Azure portal and SSL.
11
What is the effect of the default network security settings for a new virtual machine?
- Outbound requests are considered low risk, so they are allowed by default. Inbound traffic from within the virtual network is allowed. By placing a VM in a virtual network, the VM owner is implicitly opting-in to communication among the resources in the virtual network.
12
Virtual machine scale sets deploy and manage which of the following?
- This approach lets administrators easily manage hundreds of VMs without additional configuration tasks or network management.